Enable Enterprise Mobility with Advanced Remote Access Infrastructure
Empower your workforce to connect, collaborate, and operate from anywhere with Al Fuzail’s secure and scalable remote access networks. Our solutions ensure fast, reliable, and policy-controlled remote network connections, enabling businesses to maintain productivity without compromising security.
Understanding Remote Access in the Context of Today’s Distributed Enterprise
Remote access refers to the ability of users to connect to an internal corporate network or system from an external location, using a secure tunnel over the internet. In today’s distributed work environments, organizations need to ensure that remote users can access mission-critical applications, file servers, virtual desktops, and communication platforms without performance loss or data exposure.
Key Architectural Elements of a Secure Remote Access Framework
- Remote Access Gateways:
Acts as an entry point for external users connecting over public networks.
- VPN Tunnels (IPSec/SSL):
Secure encrypted pathways for data transmission across the remote network connection.
- Multi-Factor Authentication (MFA):
Adds an additional verification layer to prevent unauthorized access.
- Endpoint Security Integration:
Ensures only compliant and non-compromised devices gain access.
- Policy-Based Access Control:
Custom access privileges based on user identity, location, time, and device posture.
- Cloud-Based Remote Access:
Secure remote internet access via SASE (Secure Access Service Edge) and ZTNA (Zero Trust Network Access) models.
End-to-End Data Flow in Enterprise Remote Access Networks
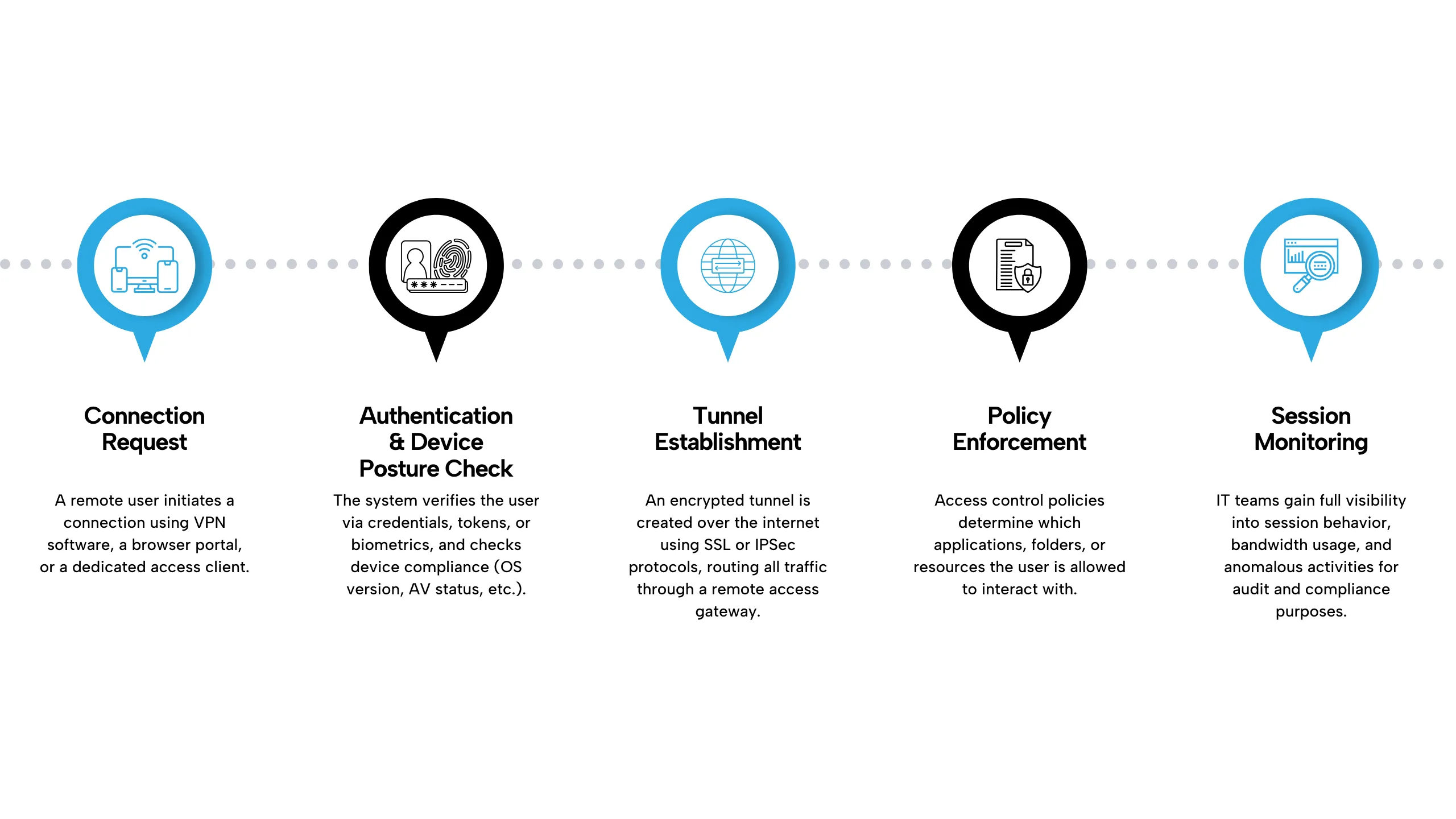
Deployment Models Tailored to Your Enterprise Remote Access Needs
Al Fuzail provides a broad range of remote access deployment models, optimized for scalability, compliance, and user experience.
Client-Based VPN
Desktop VPN clients using IPSec or SSL with MFA, split tunneling, and endpoint validation.

Clientless VPN
Secure browser-based access to internal web apps, email, or portals with no software required.

Zero Trust Network Access (ZTNA)
Identity-driven access to specific apps without exposing full networks—ideal for BYOD and contractors.

Remote Desktop Access (RDP/VDI)
Full-session remote desktops hosted on-premises or in the cloud for centralized management.

Benefits
Strategic Advantages of Choosing Al Fuzail for Remote Connectivity
Remote work is here to stay and your infrastructure must adapt. Our secure remote access solutions empower businesses to extend operations beyond physical boundaries while maintaining visibility, control, and performance.
Secure Remote Network Connection
End-to-end encryption and Zero Trust enforcement reduce the attack surface.
Scalable Access for Global Teams
Connect thousands of users across geographies without overloading the core network.
Improved User Experience
Adaptive tunnels and split-tunneling improve access speed for SaaS and internal tools.
Full Compliance & Monitoring
Audit trails, access logs, and session monitoring help meet regulatory and internal governance.
Device & Identity Validation
Block unknown or non-compliant devices using posture checks and NAC integrations.
Protect. Empower. Transform.
Why choose us?
World-Class Solutions & Services
At Fuzail Al Arabia, we offer world-class solutions tailored to your specific needs. Our team of experts provides comprehensive services.
Security and Reliability
Protect your organization from cyber threats and ensure uninterrupted access to critical resources.
Performance and Efficiency
Improve network speed, reduce costs, and simplify management.
Comprehensive Network Management
Gain full control over your network with advanced security, efficient performance, and easy management.
